The thing about mobile apps is that they are not only popular with knowledge workers, but hackers too. This makes the issue of securing the apps complex even for the professionals. Here are some of the most problematic mobile security threats usually faced by security pros.
1. Lack of a Proper Mobile Device Policy
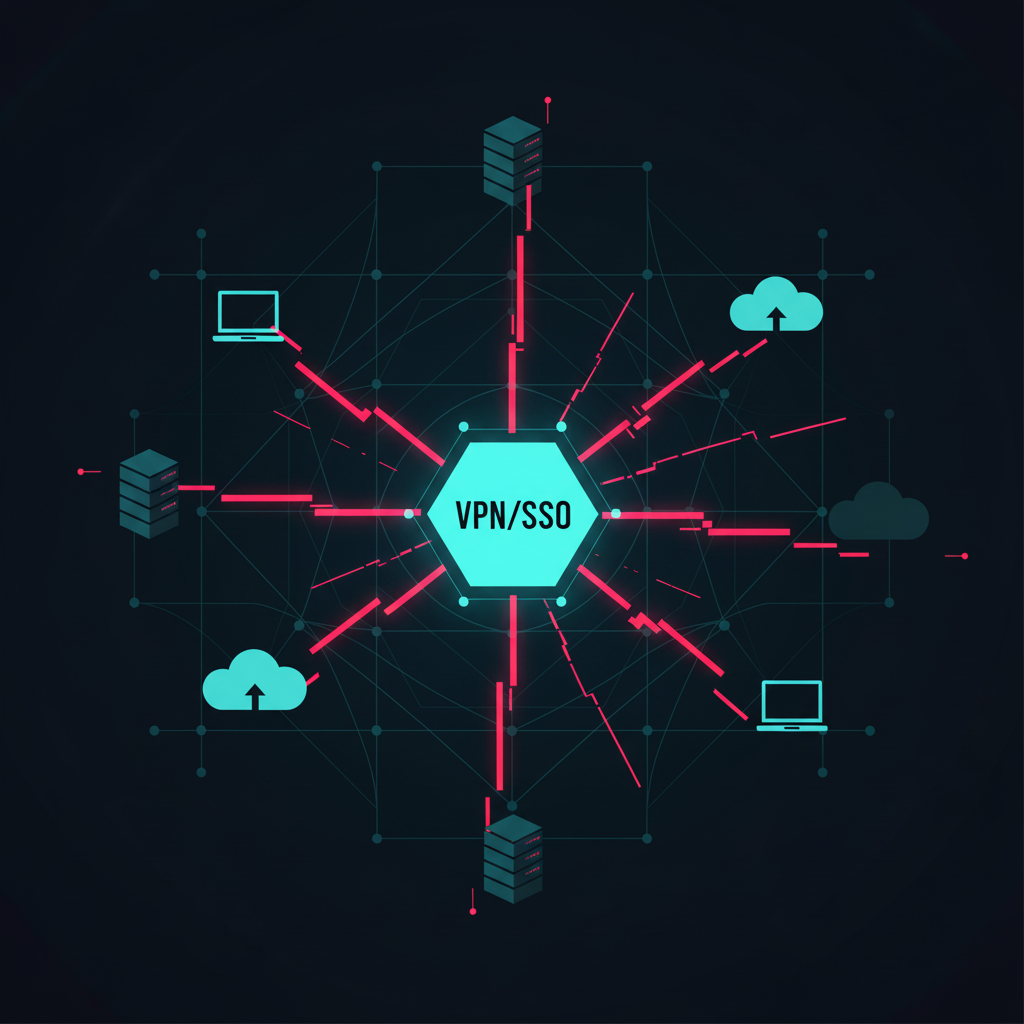
A policy should be created regarding mobile security that establishes rules for authentication. This should include credential storage. For emails and the device itself, PII restrictions should be up held. Restrictions should also be applied on passwords, PINs, and usage.
In essence, a mobile device policy should be made part of the onboarding process. It is also suggested that new employees at a company, before receiving their device or access to company resources, should read and sign off on the policy informing them of the established mobile security policy.
2. Connection Hacking
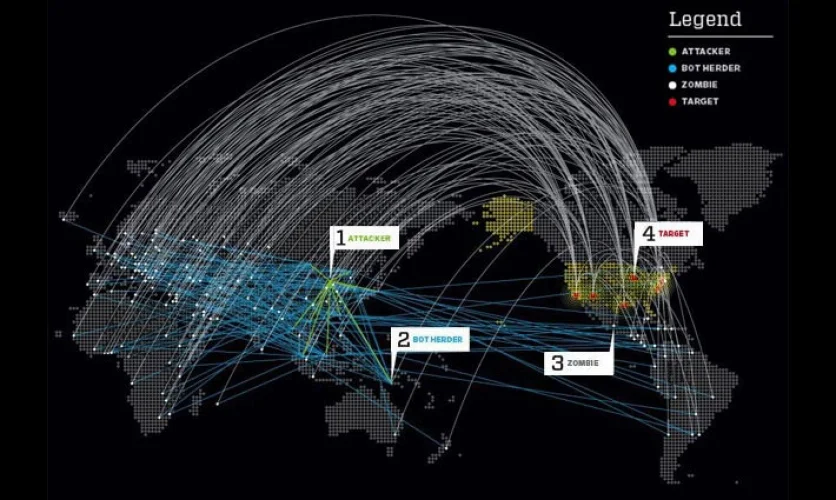
One of the most common examples of connection hacking is the ‘man-in-the-middle’ attack. Employees often use company devices to access company servers in open spaces. They might think they are safe behind the corporate firewall, but in reality, attackers set up a rogue access point and they start receiving all personal information the second they log in. This has the potential to leak a lot of sensitive data.
3. Authentication Attacks
Although not necessarily for stealing data on a mobile device, authentication consolidation will more than likely result in data specific exploits.
Industry experts predict that mobile devices will be progressively targeted for broader credential stealing. Either that, or for authentication attacks to be used at later on in the future.
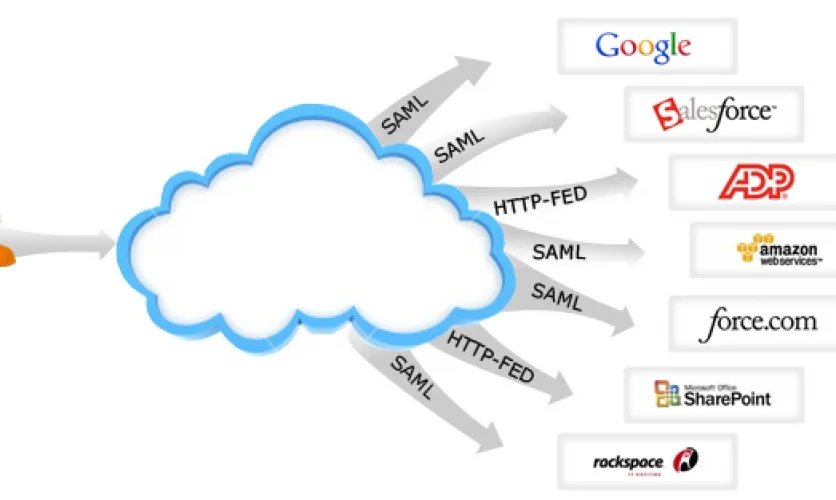
For example, think of mobile devices as a direct conduit to cloud. The cloud just keeps on getting bigger as it is provided more and more data. Almost all organizations use numerous devices (laptop, tablet, mobile, etc.) to access that data. This means that by cracking just the device, the malicious entities could have access to the ever expanding cloud filled with sensitive information.
4. Rootkits
Because of their very nature, rootkits are almost impossible to trace. Due to this, the attacker gets absolute control of the device. What is even more worrying is that it is very much possible for personal and sensitive information to be extracted through rootkits. This is especially worrying as more and more people have started to depend on mobile devices for their day to day activity. With a rootkit, malicious attackers can cause unprecedented damage.
5. Mobile Payment Security Sources
The new payment platform of Facebook uses third party resources for security. If Facebook has a Trusted Service Manager platform installed in place and agreements with the manufacturers of the handsets, for the management of secure elements, then their payment solution would introduce Facebook into classical payment. Though, this is quite difficult and Facebook may not evolve in that way.
All these points just emphasize the need for mobile app security testing. Having your app tested by the professionals will ensure that it is safe from most mobile app security threats. To avail this service and others like web application penetration testing, get in touch with us.