The SessionReaper Ultimatum: Why Penetration Testing Services Are Vital to Surviving the 'Code Freeze'
Executive Summary: Hackers are exploiting a critical Adobe Commerce flaw, CVE-2025-54236 (SessionReaper). This threat endangers Australian e-commerce during the Black Friday peak. New Privacy Act fines make the traditional "Code Freeze" risky. This report explains the threat. It shows why penetration testing services are key to securing your store without stopping sales.
The Convergence of Critical Vulnerability and Law
Q4 2025 brings two major threats. First, SessionReaper attacks the Adobe Commerce ecosystem. Second, strict Australian laws now change the cost of a data breach.
For Australian CISOs, the rules have changed. Legal and financial risks now outweigh the risk of patching during a peak.
The Threat: SessionReaper (CVE-2025-54236)
SessionReaper is a major flaw in how Adobe Commerce handles data. It lets attackers run code on your server without a login.
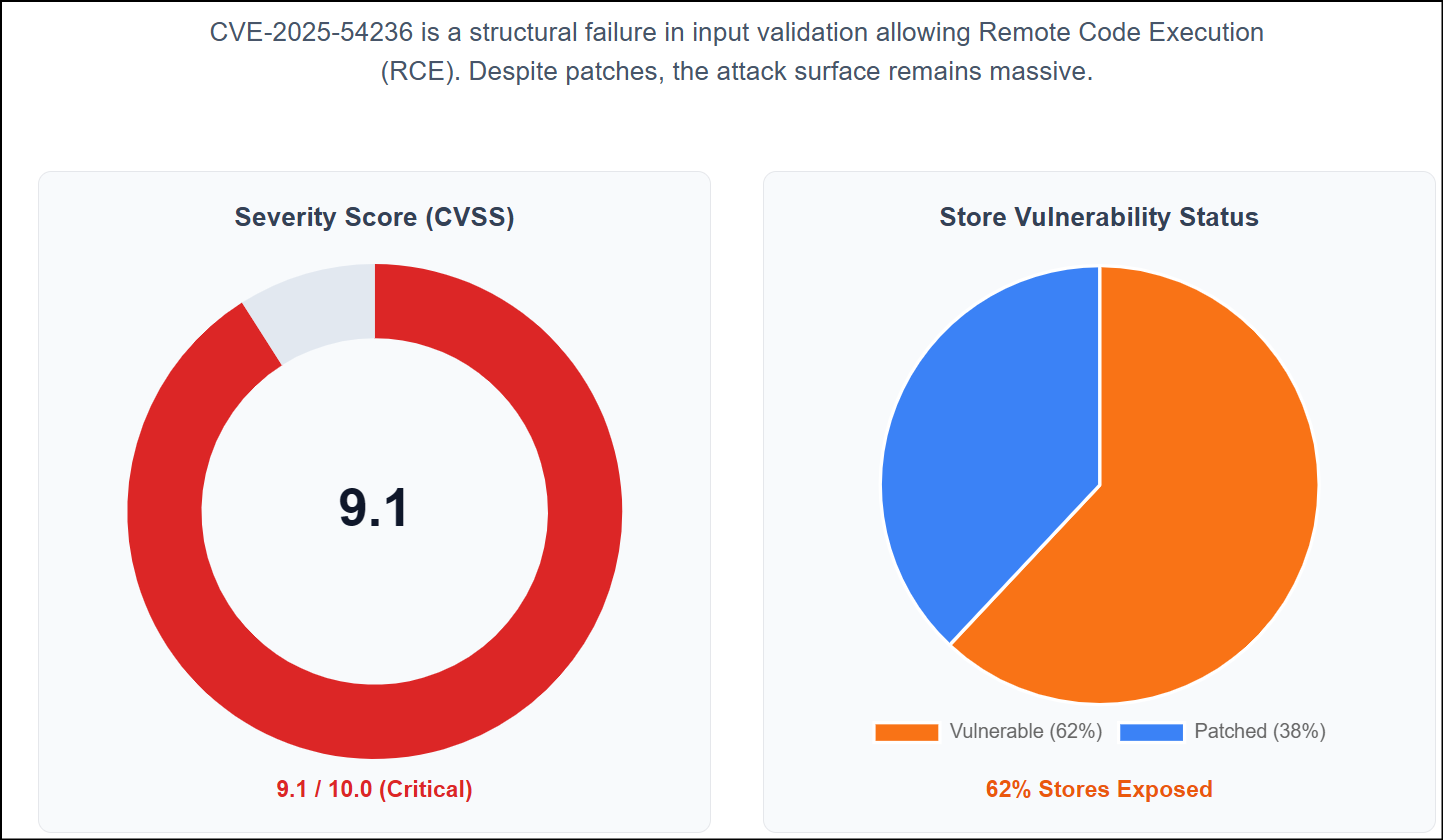
CVSS Score: 9.1 (Critical)
Vector: Remote Code Execution (RCE) via PHP Object Injection
Authentication: None required
Impact: Full server takeover, data theft, ransomware.
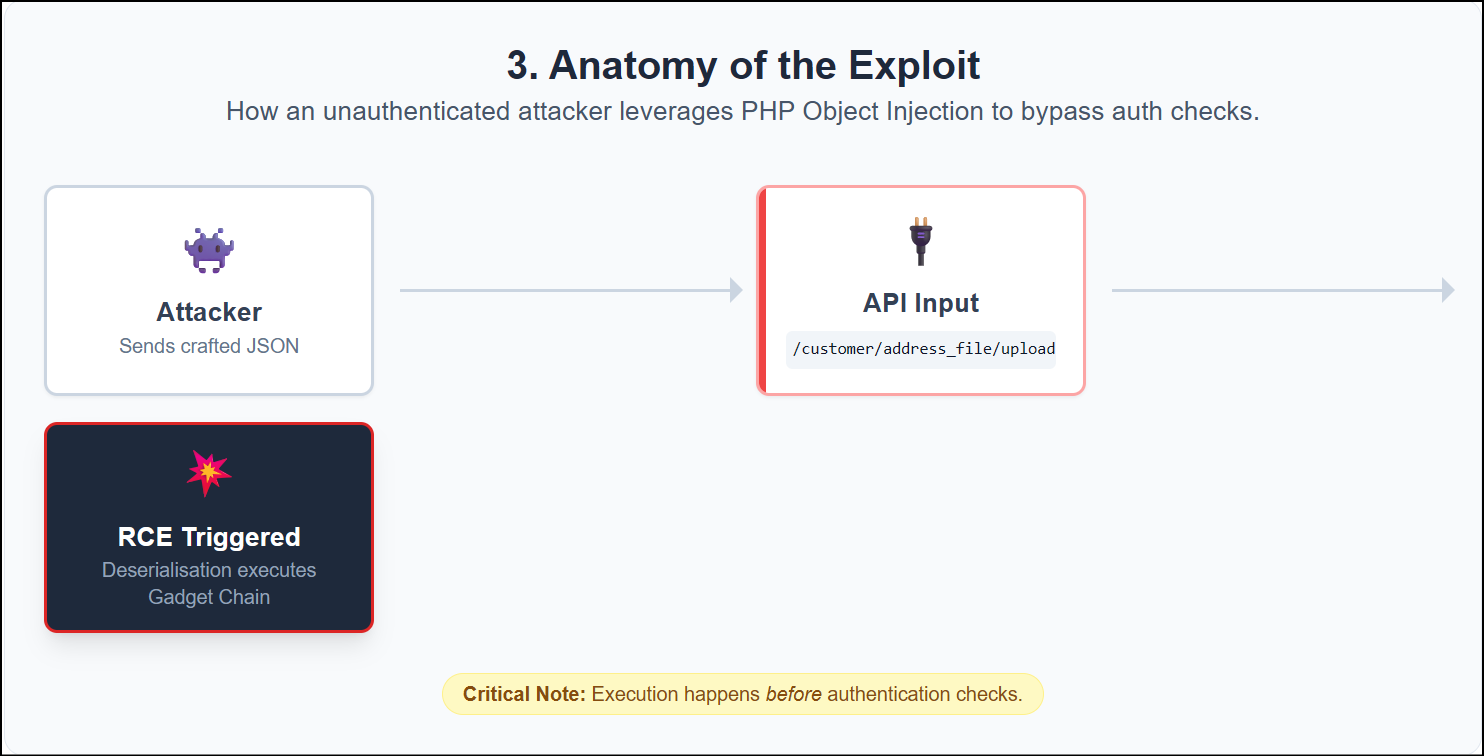
Attackers send fake data to specific API endpoints (like /customer/address_file/upload). The system trusts this input. It then runs malicious commands hidden inside the data.
The Australian Regulatory Minefield
You cannot ignore this threat just to keep the site stable.
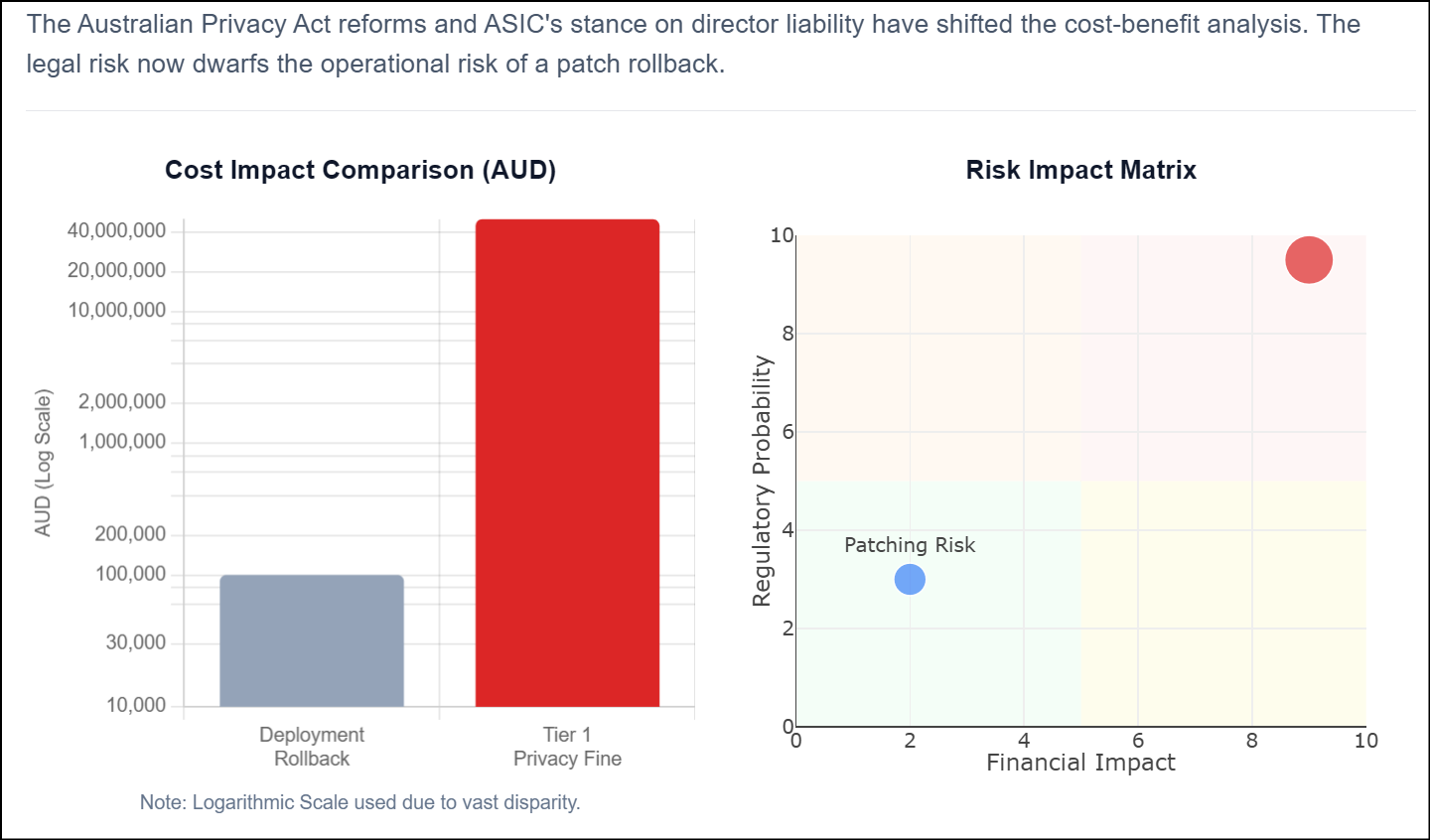
Privacy Act Reforms: "Serious interference" with privacy now costs $50 million. This penalty also applies to 30% of adjusted turnover. SessionReaper exposes customer data, creating this exact risk.
ASIC Director Liability: ASIC states that cyber resilience is a duty. Directors face personal liability for low care. Ignoring this flaw due to a "Code Freeze" helps prove negligence.
The Black Friday Dilemma: Freeze or Patch?
The "Hard Freeze" used to be standard. No changes during sales events ensured stability.
SessionReaper destroys this logic.
Sansec reports that 62% of Magento stores are unsafe. Attackers scan for these systems. A breach means attackers steal credit cards via Magecart. They could also lock your database with ransomware on Cyber Monday.
Key Takeaway: A deployment error costs money. A Tier 1 Privacy fine threatens your business survival.
Technical Deep Dive: How the Exploit Works
To understand the risk, we must look at the code. SessionReaper exploits PHP Object Injection.
The Mechanics of Failure
Data Packing: Apps turn complex data (objects) into strings to store them.
The Flaw: Adobe Commerce accepts this data from the API without checking it.
The Trigger: When the app reads (unpacks) this string, it wakes up the data object.
Gadget Chains: Attackers chain together code snippets (gadgets) already on your system.
Attackers change these gadgets to trick the server. This lets them delete files or run commands. This happens before the system checks for a login.
Why Standard Defences Fail
Firewalls often miss this. The attack looks like valid data. Your security controls must specifically check packed strings to stop it.
Strategic Response: The "Monitored Thaw"
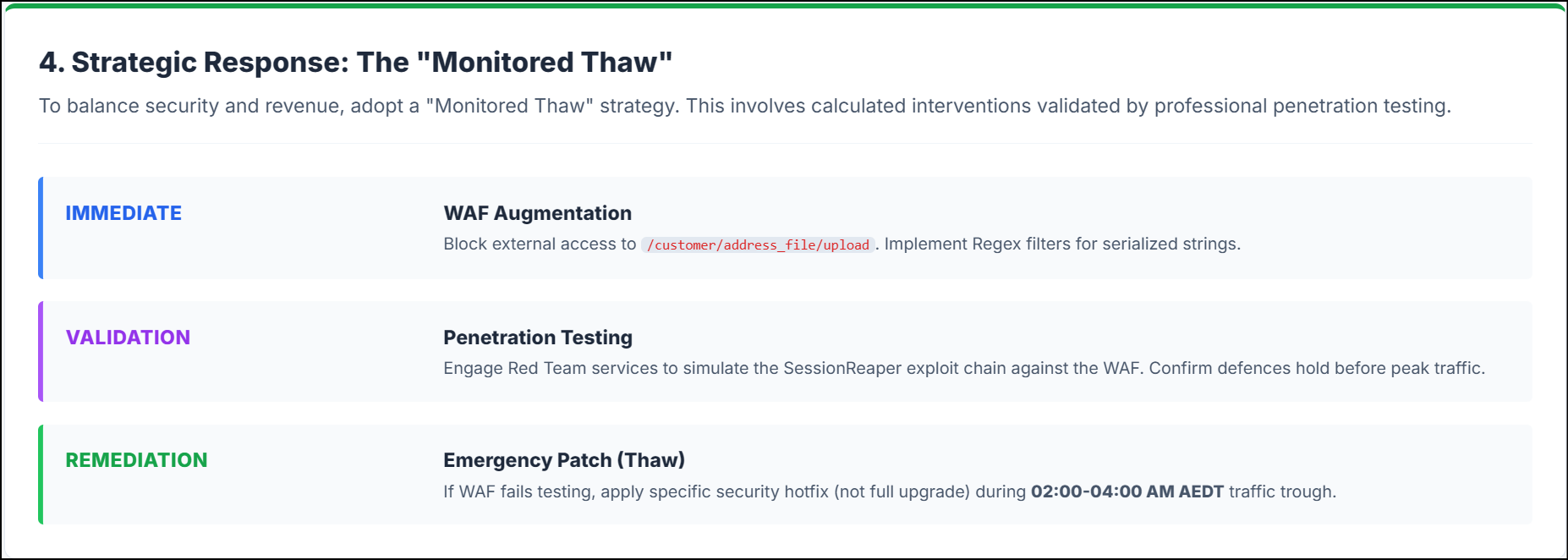
You cannot afford to ignore this. Yet, you cannot break your store during the busiest week. We recommend a "Monitored Thaw" strategy.
1. WAF Update (Immediate)
If you cannot patch now, block the attack. Configure your Web Application Firewall (WAF) to:
Block outside access to
/customer/address_file/upload.Filter requests that look like packed data (e.g., regex matching
O:\d+:).
2. Validate with Penetration Testing Services
Applying a rule is not enough; you must check if it works. Penetration testing services are vital here. A Red Team should:
Simulate real world attacks using the SessionReaper exploit.
Test if attackers can bypass your WAF rules.
Find other security weaknesses exposed by rushed changes.
Types of penetration tests needed include API testing. This proves your shields work against determined attackers.
3. The Emergency Patch
If the WAF fails, you must patch.
Isolate the Fix: Apply only the security patch. Do not upgrade the full version.
Timing: Deploy when traffic is low (typically 02:00 - 04:00 AM AEST).
Verification: Use automated tests to check checkout functions immediately.
4. Governance and Documentation
Document your choices. If a breach happens, you must prove you managed the cyber security risk. A test report proves you took reasonable steps.
Conclusion: Silence is not Security
"SessionReaper" is a clear danger. Attackers are automated. Regulators are watching.
Do not let an old "Code Freeze" policy cause a $50 million fine.
Is your WAF actually blocking SessionReaper? Are you sure?
Contact our Red Team today for a targeted web application assessment. We will validate your defences against CVE-2025-54236. We help secure your revenue without risking your reputation.