Executive summary:
Critical authentication bypass vulnerabilities in Fortinet FortiGate and related products (CVE-2025-59718 and CVE-2025-59719) are now under active attack, allowing "ghost" SSO logins that completely sidestep normal controls and logs. For Australian organisations, this is more than a VPN or firewall problem – it is a board-level exposure that directly tests whether your external penetration testing, internal penetration testing, and red team assessment services are capable of simulating SSO abuse, identity takeovers, and lateral movement across hybrid networks.
What just happened: Fortinet SSO auth-bypass under active attack
Fortinet has disclosed critical authentication bypass vulnerabilities (CVE-2025-59718 and CVE-2025-59719) affecting FortiOS, FortiProxy and FortiSwitchManager, impacting FortiCloud SSO flows into FortiGate and related appliances. These flaws allow attackers to forge or replay SSO artefacts and gain administrative access to appliances without valid credentials, effectively walking straight past login prompts and MFA.
Threat intelligence providers report malicious SSO logins and active exploitation "in the wild", with attackers using the bypass to obtain root-level control of VPN gateways and security appliances. Once an attacker owns the FortiGate, your perimeter, VPN trust boundary and network segmentation controls can be silently rewritten from the inside, turning your firewall into the attacker's beachhead.
Key takeaways for boards and CISOs:
- This is not a theoretical CVE; exploitation has already started.
- Compromise of the FortiGate tier effectively neutralises network security controls.
- Traditional penetration testing methods that only "scan and report" will miss SSO-centric and identity-abuse paths.
Why this incident reframes "what is penetration testing" for modern enterprises
At board level, "what is penetration testing" is changing from a narrow view of port scanning and basic exploitation to a broader application security assessment across identity, SSO, and cloud edge devices. Attacks on Fortinet SSO show how real adversaries chain weaknesses across VPNs, SAML/OIDC flows, RBAC misconfigurations and internal lateral movement to achieve business impact.
Modern penetration testing services in Australia must therefore validate not just internet-facing ports, but also:
- The integrity of SSO and identity federation to VPNs, admin portals and cloud consoles.
- Whether a compromised VPN appliance or identity token can be used to bypass network segmentation and reach crown-jewel systems.
For Australian organisations subject to PCI DSS, GDPR, or the Cyber Security Act 2024, boards need assurance that penetration testing is aligned to real-world attack paths – especially those starting at identity and VPN infrastructure.
How Fortinet SSO attacks actually work (and why scanners alone won't save you)
Authentication bypass through SSO flows
The Fortinet flaws centre on improper verification of SSO tokens and cryptographic assertions in FortiCloud SSO, enabling authentication bypass on FortiOS, FortiProxy and related components. In practice this means an attacker can submit crafted or replayed SAML/OIDC-style artefacts or exploit validation gaps to appear as a legitimate SSO user – often with administrator-level rights.
Once logged in as a "ghost" admin, attackers can:
- Change VPN and firewall policies to open backdoors and exfiltration paths.
- Create new trusted SSO configurations or local admin accounts that persist beyond patching.
- Disable logging, alter log destinations, or route logs to attacker-controlled collectors.
From VPN edge to complete network takeover
Observed exploitation patterns show a two-stage progression: first, auth bypass to gain control of the management plane; second, pivoting from the appliance into internal networks and management tools. With root-level control of a VPN gateway, an attacker can impersonate users, inject routes, and access internal services as if they were a trusted remote employee.
This adversary behaviour is beyond what a basic vulnerability assessment or simple penetration testing tool list will detect, because:
- Scanners tend to focus on version detection and known signatures, not subtle SSO state logic.
- Many organisations treat VPNs and firewalls as "out of scope" for application security assessment, leaving a blind spot between network penetration testing and web application penetration testing.
Vulnerability assessment vs pen test: why boards must care
Many organisations still use "vulnerability assessment vs pen test" interchangeably, but Fortinet SSO exploitation demonstrates why the distinction matters at the governance level.
| Aspect | Vulnerability Assessment | Penetration Testing |
|---|---|---|
| Approach | Automated scanning for known CVEs and misconfigurations. | Manual exploitation of authentication flows, SSO logic, and chained weaknesses. |
| Output | Point-in-time lists of issues, ranked by CVSS but often without business context. | Evidence-based scenarios demonstrating how an attacker could turn a Fortinet auth bypass into data theft, ransomware spread, or regulatory breach. |
| Board Value | Inventory of risks. | Proof of realistic breach paths and mitigation priorities. |
For CISOs, vulnerability assessment vs pen test is no longer a technical nuance; it is a question of whether the organisation has realistic evidence on how its identity and VPN stack would withstand a modern attack.
Mapping Fortinet SSO risk to penetration testing methods
To address this class of exposure, organisations should revisit penetration testing methodology and ensure it explicitly covers identity and SSO-driven threats.
External penetration testing
A modern external penetration testing engagement should now:
- Enumerate VPN, SSO, and edge appliances (FortiGate, Citrix, Palo Alto, ZTNA, CASB) as first-class targets.
- Attempt controlled abuse of SAML/OIDC, FortiCloud SSO and other federation mechanisms, not just open ports.
Internal penetration testing
Internal penetration testing then assumes the Fortinet layer has been compromised and asks, "What happens next?"
- Can a fake "VPN user" pivot from remote access networks to core AD, ERP and OT segments?
- Are EDR, NAC and micro-segmentation controls effective once an attacker is "inside the wire" with legitimate-looking network paths?
Web and API penetration testing
Because FortiGate typically fronts critical web applications and APIs, web application penetration testing and API penetration testing should be integrated into the same scenario.
- Test whether compromised VPN or reverse-proxy tiers weaken rate-limiting, WAF rules, or API authentication.
- Validate that tokens and sessions issued behind the VPN comply with least privilege and cannot be abused to escalate across tenants or environments.
Red team assessment services: simulating SSO and VPN abuse
Where penetration testing stops at enumeration and exploitation of specific hosts, red team assessment services simulate a persistent adversary who will chain multiple weaknesses to reach strategic objectives.
A mature red team scenario for Fortinet SSO risk should include:
- Phishing or credential theft to obtain low-privilege SSO accounts, followed by attempts to exploit auth-bypass flaws.
- Use of compromised FortiGate to reconfigure VPN split-tunnelling, routing, and DNS to quietly access backup networks, directory services and cloud control planes.
- Emulation of data staging, exfiltration and ransomware deployment pathways that start from the VPN tier rather than a traditional desktop compromise.
Regulatory and compliance implications for Australian organisations
Australia's Cyber Security Act 2024 and the new mandatory ransomware and cyber extortion payment reporting obligations mean that poorly secured VPN and SSO infrastructure now has regulatory as well as technical consequences.
- From 30 May 2025, Australian businesses above a $3 million turnover must report ransomware and cyber-extortion payments to ASD within 72 hours, regardless of payment size.
- Failure to report can attract civil penalties, and regulatory scrutiny is increasingly focused on whether "reasonable steps" were taken to protect networks and data before the incident.
For PCI DSS penetration testing and GDPR penetration testing obligations, a compromised VPN or firewall that exposes cardholder or personal data would be viewed as a preventable control failure if critical auth-bypass patches were missed or if testing scope excluded SSO and VPN infrastructure.
Board-level implications:
- Penetration testing for cloud security and VPN/SSO must be explicitly in scope for compliance attestations.
- Penetration testing price in Australia should be evaluated against the potential cost of a reportable ransomware event and associated regulatory penalties.
Building a modern penetration testing roadmap around identity and VPN risk
CISOs and IT Directors should use the Fortinet incident as a forcing function to modernise their penetration testing roadmap.
Prioritise identity-aware testing
- Integrate web application penetration testing, API penetration testing, and SSO abuse scenarios into core testing programmes, not as add-ons.
- Ensure penetration testing methods include manual review of SSO logic, JWT/SAML validation, RBAC enforcement and session management beyond automated scanning.
Cover the full technology stack
Your roadmap should explicitly call out:
- Network penetration testing that includes VPNs, firewalls, and SD-WAN controllers as high-value assets, not "plumbing".
- Internal penetration testing focused on lateral movement from VPN and privileged network zones into Active Directory, databases, and cloud management environments.
- Cloud penetration testing for IaaS, PaaS and SaaS, ensuring misconfigured SSO and conditional access policies are identified early.
- Mobile application penetration testing and IoT penetration testing for scenarios where remote staff, field devices or OT gateways rely on FortiGate or similar VPN infrastructure.
Make it accessible for small and mid-market businesses
Fortinet is widely deployed in small and mid-market Australian organisations, not just large enterprises. Penetration testing for small business therefore needs:
- Right-sized packages that still include VPN/SSO testing, not just a basic external scan.
- Clear penetration testing quote options that show what is covered (and what is not) so boards can make informed risk decisions.
Visualising the attack path: from FortiGate to data loss
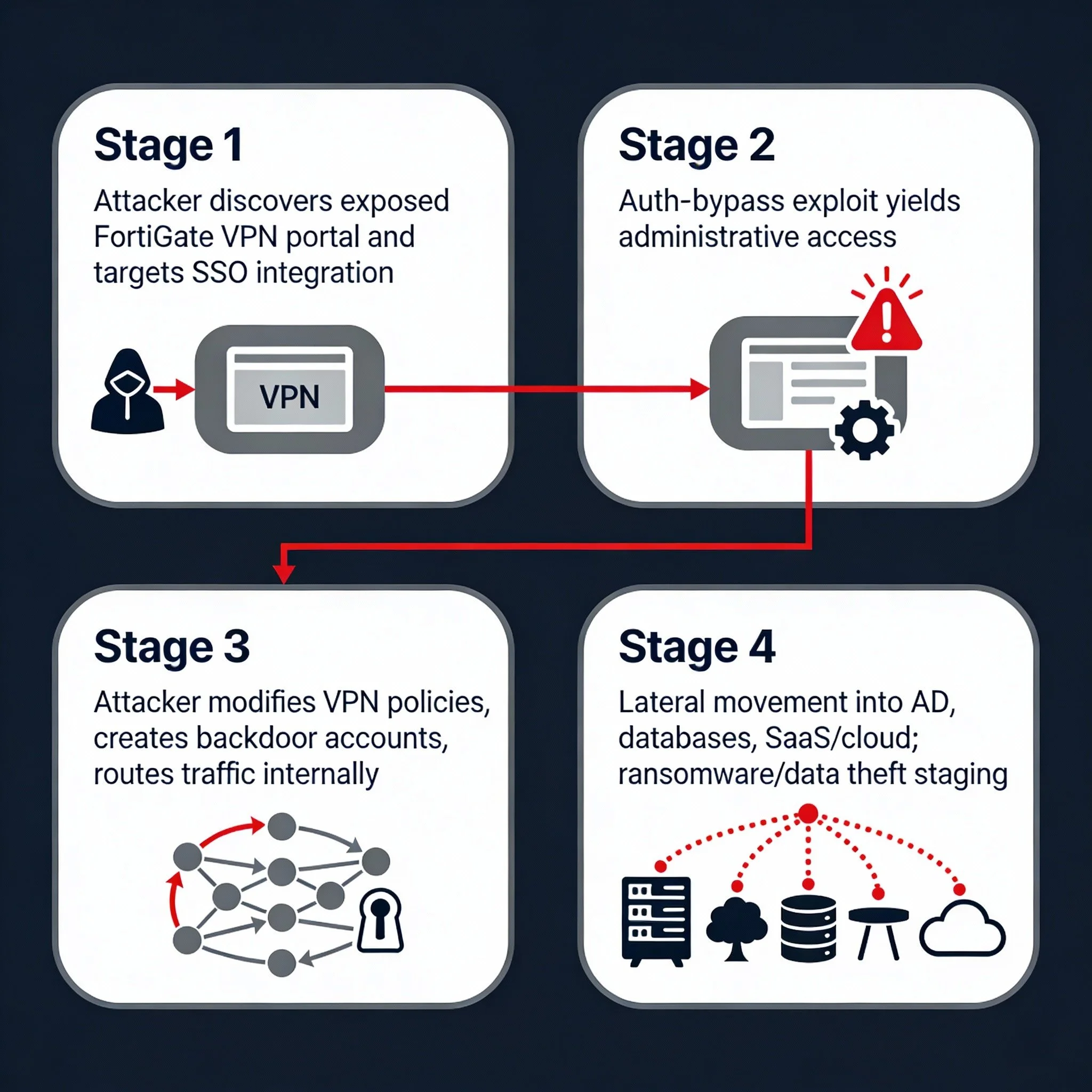
Below is a simple conceptual diagram that helps boards understand the Fortinet SSO attack chain:
Stage 1: Attacker discovers exposed FortiGate VPN portal and targets SSO integration.
Stage 2: Auth‑bypass exploit yields administrative access to FortiGate management.
Stage 3: Attacker modifies VPN policies, creates backdoor accounts, and routes traffic into internal networks.
Stage 4: Lateral movement into AD, databases, SaaS and cloud consoles; staging for ransomware or data theft.
How to engage: penetration testing services Australia should be demanding
In light of these Fortinet SSO vulnerabilities and the broader ransomware reporting landscape in Australia, organisations should look to hire a penetration tester or penetration testing company Australia that can demonstrate:
- Proven experience testing VPNs, SSO, and identity-centric attack paths – not just generic web testing.
- A clear penetration testing methodology that covers external penetration testing, internal penetration testing, cloud penetration testing, and application security assessment in a single, cohesive programme.
- Transparent guidance on penetration testing services Australia-wide, including realistic penetration testing price Australia figures and options to book a pen test aligned to your financial year and regulatory deadlines.
For boards, the question is no longer "penetration testing vs vulnerability assessment", but "are we testing the systems attackers are actually targeting – our VPNs, SSO, and cloud edge – with realistic adversary techniques?"
Call to action:
If your organisation relies on Fortinet or similar VPN and SSO infrastructure, now is the right time to schedule an integrated external, internal and application penetration testing engagement focused on identity and VPN abuse scenarios. Engage a specialist penetration testing company in Australia that can provide a tailored penetration testing roadmap, a clear penetration testing quote, and red team assessment services to validate your readiness against the next wave of SSO-driven attacks.