Strategic Threat Report: The Akira-SonicWall Campaign and its Implications for Australian Businesses
Executive Briefing: A Perfect Storm of Technical, Criminal, and Regulatory Risk
In September 2025, Australian businesses are confronted by a uniquely dangerous convergence of threats that elevates the risk of a cyber incident from a technical problem to a board-level governance crisis. This perfect storm is composed of three distinct but interconnected elements: a critical technical failure, a sophisticated criminal enterprise, and a new, unforgiving regulatory minefield.
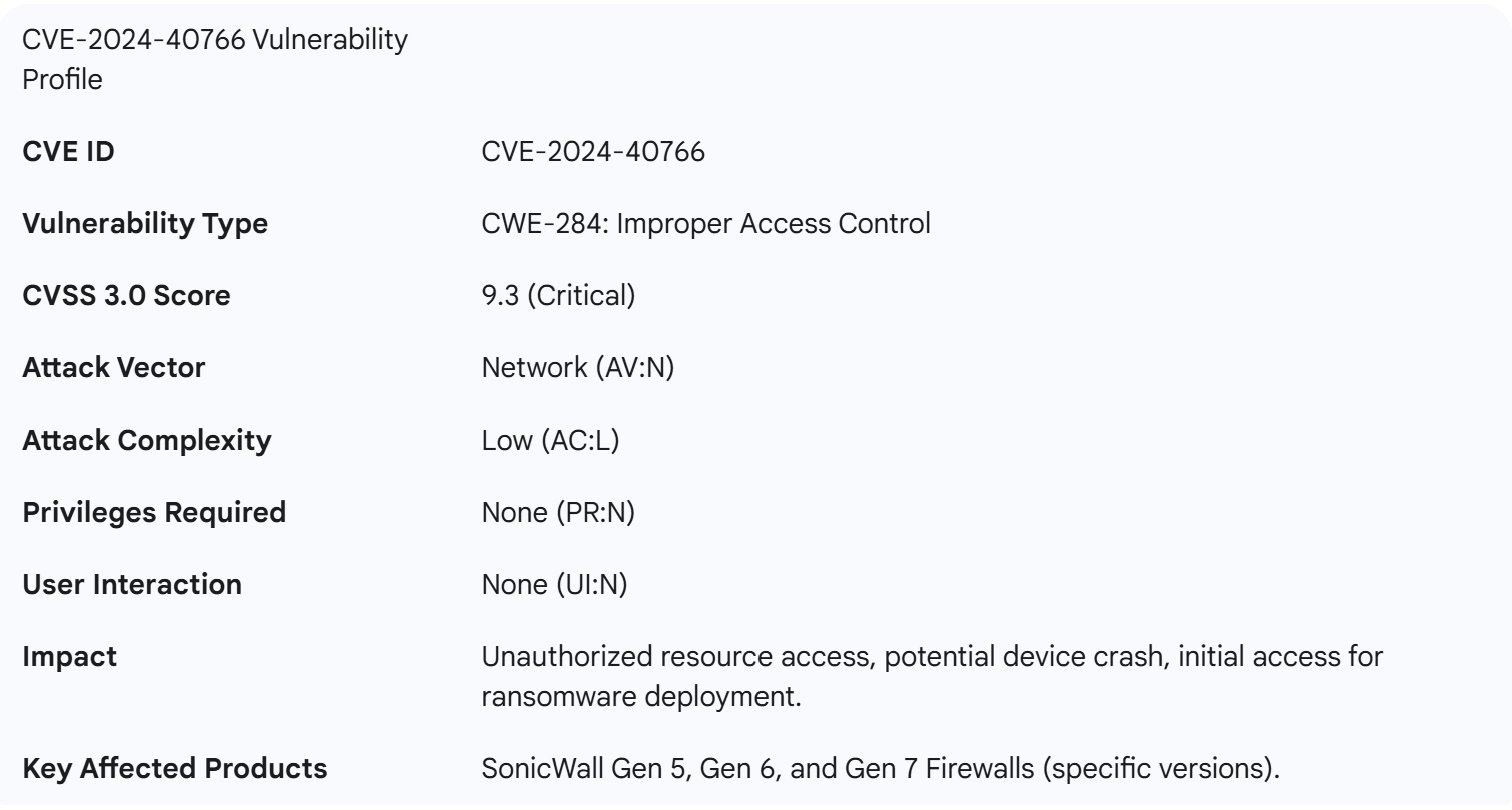
The foundation of this threat is a critical, remotely exploitable vulnerability, identified as CVE-2024-40766, affecting a wide range of SonicWall SSL VPN devices. These devices are a common feature in Australian corporate networks, serving as the primary gateway for remote access and making them a high-value target for malicious actors. The vulnerability's severity is compounded by the fact that it is being actively and aggressively exploited in the wild.
Capitalizing on this technical weakness is the Akira ransomware group, a financially motivated and highly capable criminal organization. Intelligence confirms that Akira is specifically leveraging the SonicWall vulnerability as an initial access vector to compromise Australian organizations, particularly small and medium-sized businesses and critical infrastructure entities. Once inside a network, the group employs a double-extortion model, exfiltrating sensitive data before encrypting critical systems, thereby maximizing pressure on victims to pay a ransom.
The most significant factor amplifying this threat is the recent evolution of Australia's legal and regulatory landscape. This campaign is unfolding just months after the commencement of the new Mandatory Ransomware Payment Reporting regime under the Cyber Security Act 2024 on May 30, 2025. This legislation, along with a new statutory tort for serious invasions of privacy that took effect in June 2025, dramatically increases the legal, financial, and reputational consequences of a successful ransomware attack. An organization that suffers a breach and pays a ransom is now legally obligated to create an official, detailed record of its security failure with the Australian Signals Directorate (ASD). This formal declaration of a vulnerability exploitation can trigger a cascade of further regulatory scrutiny from bodies like the Office of the Australian Information Commissioner (OAIC) and the Australian Securities and Investments Commission (ASIC), while also providing potent evidence for class-action lawsuits.
This convergence means that the cost of the Akira-SonicWall compromise is no longer limited to the ransom payment and IT recovery expenses. It now encompasses a severe and predictable chain of regulatory penalties, legal liabilities, and profound reputational damage. In this heightened-risk environment, traditional, compliance-focused security measures are insufficient. Proactive, adversary-emulation-based security validation, such as penetration testing, has become a non-negotiable strategic imperative for any organization seeking to manage this multifaceted risk.
URGENT ACSC alert: Akira ransomware is exploiting SonicWall VPNs (CVE-2024-40766). This one-minute briefing explains the patching paradox — why applying patches alone can still leave networks exposed via old credentials — and shows the business impact: data theft, ransomware and new 2025 regulatory fines. Learn how Lean Security’s adversary simulations and human-led penetration testing validate real-world defences and reveal hidden access paths before attackers do. If you manage IT for an Australian business, don’t guess — test like an attacker. Click the link or contact info@leansecurity.com.au | www.leansecurity.com.au | +61 (2) 8078 6952
Technical Deconstruction of the Attack Vector: CVE-2024-40766
To fully appreciate the urgency of the current threat, a precise understanding of the underlying technical vulnerability is essential. The core of the Akira campaign's success lies in its exploitation of CVE-2024-40766, a flaw that fundamentally undermines the security of a critical network perimeter device.
The vulnerability is officially classified as an improper access control issue, cataloged under Common Weakness Enumeration (CWE) ID CWE-284. It resides within the SonicOS management access and Secure Sockets Layer (SSL) Virtual Private Network (VPN) functionality. In essence, the flaw allows an attacker to circumvent the security mechanisms that are supposed to verify a user's identity and permissions before granting access to the network.
The severity of this vulnerability is reflected in its Common Vulnerability Scoring System (CVSS) v3.0 score of 9.3 out of 10.0, which is rated as "Critical". This high score is a result of several key characteristics. The attack can be launched remotely over a network, requires no prior privileges or authentication, and needs no interaction from a legitimate user, making it simple for an attacker to exploit. Successful exploitation allows a remote, unauthenticated attacker to bypass authentication mechanisms, gain unauthorized access to sensitive internal network resources, and, under certain conditions, cause the firewall itself to crash, leading to a denial-of-service condition.
The scope of affected products is extensive, covering multiple generations of SonicWall's firewall appliances. This includes Gen 5 (specifically SOHO models), Gen 6, and Gen 7 firewalls running specific older firmware versions. This broad range ensures that a significant number of Australian businesses, from small offices to larger enterprises, are potentially exposed. A particularly critical point of risk is that some older, End-of-Life (EoL) devices, such as the NSA 2600 and other Gen 5 models, will not receive security patches for this vulnerability, leaving them permanently exposed unless decommissioned or isolated from the network.
The exploit mechanics involve an attacker sending specially crafted input during the authentication process to the SSL VPN interface. This malformed input tricks the system's flawed authentication algorithm, allowing the attacker to either hijack an existing, legitimate user's active SSL VPN session or gain privileged access directly. This provides the attacker with a direct foothold inside the corporate network, from which they can begin the next phases of their attack, including reconnaissance, lateral movement, and the eventual deployment of ransomware.
Threat Actor Dossier: Akira Ransomware
Understanding the vulnerability is only half the battle; it is equally critical to understand the adversary exploiting it. The threat actor in this campaign, known as Akira, is a formidable and well-documented ransomware group that has demonstrated both technical sophistication and financial motivation since it first emerged in March 2023.
Akira operates on a Ransomware-as-a-Service (RaaS) model. This means the core developers of the ransomware and its associated infrastructure provide their tools to a network of affiliates, who are then responsible for carrying out the attacks. In return, the developers receive a percentage of any ransom payments collected. This model allows the group to scale its operations rapidly and leverage a diverse range of affiliate skill sets, making their tactics, techniques, and procedures (TTPs) varied and difficult to predict. While primarily targeting small-to-medium enterprises, their victims span all sectors and geographic regions, including a noted focus on the United States, Western Europe, and, more recently, Australia.
The group's primary method for gaining initial access to target networks is by compromising internet-facing services, particularly VPNs. They are known to exploit both known, unpatched vulnerabilities, such as CVE-2024-40766, and to use valid credentials that have been stolen or purchased from dark web marketplaces.
Once initial access is achieved, Akira affiliates execute a well-defined post-exploitation playbook designed to maximize impact while evading detection. They make extensive use of "Living-off-the-Land" (LotL) techniques, which involve using legitimate, pre-installed system tools to carry out their malicious activities. This approach makes their actions difficult to distinguish from normal administrative activity, often bypassing traditional antivirus and even some Endpoint Detection and Response (EDR) solutions. Key post-exploitation TTPs include:
Persistence and Defense Evasion: Akira affiliates often deploy legitimate remote access software like AnyDesk or ScreenConnect to maintain a persistent foothold in the compromised network. To disable defenses and prevent recovery, they use built-in Windows utilities like
vssadmin.exeto find and delete Volume Shadow Copies (system backups).Credential Access and Lateral Movement: A primary objective after gaining entry is to escalate privileges. Attackers have been observed dumping credentials from the Local Security Authority Subsystem Service (LSASS) process memory, using pass-the-hash techniques to impersonate users, and moving laterally across the network via the Remote Desktop Protocol (RDP) to compromise high-value targets like domain controllers.
Data Exfiltration: Before deploying the final ransomware payload, Akira engages in data exfiltration as part of its double-extortion strategy. Affiliates use common archiving tools like WinRAR to compress sensitive data and then exfiltrate it using FTP clients like FileZilla or cloud-syncing tools such as Rclone. This stolen data is used as leverage, with the threat of public release if the ransom is not paid.
Impact: The final stage of the attack involves the deployment of their encryptor, which exists in both C++ and Rust-based variants. This malware encrypts files across the network, appending a
.akiraextension and rendering them inaccessible. A ransom note is then left behind with instructions for payment, typically in Bitcoin.
The following table maps some of Akira's observed TTPs to the industry-standard MITRE ATT&CK® framework, providing a structured view of their attack methodology.
The Australian Attack Vector: Why Patches Are Not Enough
One of the most alarming aspects of the ongoing Akira campaign in Australia is a critical nuance that creates a dangerous false sense of security for many organizations. An analysis of the attack timeline reveals a significant paradox: the vulnerability was first disclosed and patched by SonicWall in August 2024, yet the Australian Cyber Security Centre (ACSC) issued its high-severity alert regarding ongoing active exploitation more than a year later, on September 10, 2025. This indicates that the attacks are not solely succeeding against organizations that failed to patch; they are also succeeding against organizations that believe they have remediated the issue.
The root cause of these continued breaches lies in the gap between a simple compliance action—applying a software patch—and achieving true security resilience. The successful attacks are exploiting a procedural failure, not just a software flaw. The core issue is the failure of organizations to reset all local SSL VPN user account passwords after applying the patch. This is particularly prevalent in environments that have migrated their configurations and user accounts from older Gen 6 hardware to newer Gen 7 devices, carrying over the potentially compromised credentials in the process.
This procedural oversight is the key that Akira is using to unlock patched networks. The attack sequence often unfolds as follows:
Prior to August 2024, an organization's SonicWall device was vulnerable to CVE-2024-40766.
During this period of vulnerability, threat actors (or automated scanners) exploited the flaw to harvest a list of valid SSL VPN user credentials.
The organization's IT team, following best practices, applied the security patch released by SonicWall, closing the technical vulnerability.
However, the team did not force a password reset for all local SSL VPN user accounts.
Akira affiliates, now armed with the previously stolen credentials, return to the patched device. While they can no longer exploit CVE-2024-40766 directly, they can simply log in as a legitimate user with the compromised password, gaining the same level of network access.
This scenario exposes a fundamental weakness in a compliance-driven security posture. An automated vulnerability scanner will scan the device, confirm the patch has been applied, and report the system as "secure". Security metrics will show 100% compliance with the patching directive. Yet, from the adversary's perspective, the network remains completely accessible. This demonstrates that security is a holistic process, not a series of disconnected actions. The patch fixed the vulnerable code, but it did not remediate the consequences of the period of exposure—namely, the compromised credentials.
Only a human-led, goal-oriented security assessment, such as a penetration test, can uncover this type of process-based risk. Such an assessment would not stop at verifying the patch; it would simulate the adversary's actual TTPs, including attempting to use known or suspected compromised credentials to gain access. This approach validates true resilience, not just checklist compliance, and is the only way to be certain that the door is truly locked.
Business Impact Analysis: Quantifying the Cost of Compromise in 2025
A successful breach by the Akira ransomware group leveraging the SonicWall vulnerability will inflict severe and multifaceted damage on an Australian business. The impact extends far beyond immediate operational disruption and encompasses direct financial costs, long-term reputational harm, and, crucially, a complex and perilous web of new regulatory and legal liabilities specific to the 2025 landscape.
The direct financial costs are substantial and immediate. They include the ransom demand itself, which for Akira victims has been significant, with the group extorting over $42 million USD in its first year of operation. Beyond the ransom, organizations face extensive costs for incident response and digital forensics services, legal counsel to navigate the breach, and technical services for data recovery and system restoration.
Operational disruption can be catastrophic. The encryption of critical systems halts business operations, leading to lost revenue and productivity. As seen in other major cyberattacks, such as the one affecting Jaguar Land Rover, these disruptions can cascade through the supply chain, impacting partners and suppliers and causing widespread economic damage.
However, for Australian businesses in 2025, the most dangerous consequences are now rooted in the new legal and regulatory framework. A ransomware incident is no longer a private crisis to be managed internally; it is a public event with mandatory reporting obligations and significant legal exposure.
Mandatory Ransomware Payment Reporting: Under the Cyber Security Act 2024, any business with an annual turnover exceeding $3 million that makes a ransom payment must report it to the ASD within 72 hours. This report is not a simple notification. It requires detailed information about the incident, the threat actor, the payment, and, most importantly, the vulnerabilities that were exploited. This creates a formal, official record of the security failure. While the government has adopted an "education first" approach for the initial phase, this ends on December 31, 2025, with active compliance and enforcement beginning in January 2026.
Notifiable Data Breaches (NDB) Scheme: If the data exfiltrated by Akira includes personal information, the incident will also trigger obligations under the NDB scheme, requiring notification to the OAIC and affected individuals. Failure to comply can result in significant penalties.
Statutory Tort for Serious Invasion of Privacy: Effective from June 10, 2025, individuals now have a personal right of action to sue for serious invasions of privacy. A data breach resulting from a ransomware attack is a prime candidate for class-action lawsuits under this new tort, with courts empowered to award damages for emotional distress.
ASIC and Director's Duties: Regulators, particularly ASIC, are increasingly viewing cyber resilience as a fundamental component of a director's duty of care and diligence. A failure to adequately prepare for and respond to a known and widespread threat like the Akira-SonicWall campaign could be viewed as a breach of these duties, exposing company directors to personal liability.
To assist executives in navigating these new requirements, the following checklist summarizes the key obligations under the mandatory ransomware reporting regime.
Simulating the Adversary: Penetration Testing for the Akira Threat Model
Given the procedural nature of the ongoing Akira-SonicWall campaign and the inadequacy of automated compliance checks, the only reliable method to validate an organization's defenses is through proactive, human-led adversary simulation. A comprehensive penetration test designed to mimic the specific threat model of Akira is essential to move beyond a false sense of security and achieve genuine resilience.
Standard vulnerability scanning is insufficient because it is designed to identify known software flaws and misconfigurations at a specific point in time. As established, it would likely report a patched SonicWall device as secure, completely missing the critical risk posed by compromised credentials that were not reset. A true security assessment must test not only the technology but also the processes and people that constitute the overall security posture.
A specialized SonicWall Security Assessment & Adversary Emulation Service would provide the necessary assurance by directly addressing the TTPs used by Akira in this campaign. Such a service would be structured around three key phases:
External Penetration Test: This phase focuses on the network perimeter. The testing team would specifically target the organization's SSL VPN endpoints, attempting to identify not only CVE-2024-40766 but also other common vulnerabilities and misconfigurations associated with remote access services. This validates the strength of the external-facing attack surface.
Configuration and Process Review: The team would conduct a thorough review of the SonicWall device configurations. This goes beyond checking the firmware version. It involves looking for procedural weaknesses, such as the use of insecure default user groups, an exposed Virtual Office Portal that could facilitate MFA manipulation, and the absence of robust account lockout policies. This step directly assesses the organization's resilience against the credential-based attacks that are bypassing patched systems.
Assumed Breach Scenario / Red Teaming: In the most critical phase, the testing team simulates a successful initial breach, mimicking Akira's post-exploitation playbook (as detailed in the MITRE ATT&CK table above). From a low-privilege foothold inside the network, the team would attempt to escalate privileges, dump credentials from LSASS, move laterally using RDP, and evade detection by EDR and other security controls using LotL techniques. This phase provides a true measure of the organization's ability to detect, respond to, and contain a real-world intrusion.
The final report from such an engagement would provide far more value than a simple list of vulnerabilities. It would deliver a narrative of the simulated attack, mapping out the potential paths an adversary like Akira could take through the network. The recommendations would be actionable and prioritized, focusing not just on technical fixes but on the procedural and architectural improvements needed to disrupt the entire attack chain and build lasting security resilience.